Social Engineering Explainer: Webinar Recap with Video and Text Option
On January 29, 2020, Ankura Consulting and KMRD Partners partnered to host a free webinar on how social engineering. Watch the webinar as Brian Heun and Clay Blankenship explain how cybercriminals use social engineering to manipulate employees into divulging sensitive information and how organizations can protect employees and secure assets from cyber attacks.
You can watch a replay of the webinar on Youtube.
Contact Brian Heun at 267-482-8309 or email bheun@kmrdpartners.com to have an expert review your cyber and crime coverage or to find out more about cyber insurance discounts for your business.
Below is the text version of our Social Engineering Webinar
As promised, we’ve made available our video and lightly edited text version of our recent webinar called “Social Engineering Webinar: How Criminals Exploit Human Behavior and How to Protect Your Enterprise.” You will find the Q&A below the text version and some are edited for clarity.
Chris: Thank you so much for joining this webinar on Social Engineering. Today we’re going to be discussing how criminals exploit human behavior and how to protect your computer and business from cyber intrusion.
Clay: Good morning everybody. My name is Clay Blankenship. I’m a Managing Director with Ankura Consulting. I’m retired law enforcement. I had 22 years and my last seven were in a cyber crime unit where I created the cyber crime unit instead of the digital forensics lab. I investigated anything that was cyber-related in law enforcement. I made the bounce to incident response in the corporate world where I went to work for IBM on their global incident response team – and then was later hired by Navigate Consulting, which was then purchased by incur. So I’ve been here for about three years. I have a wide range of experience dealing with the computer forensics and incident response, and investigated everything from gang activity, homicides, network intrusions, ransomware, email compromise, and a number of different cases. And I’m also a digital forensics instructor.
Clay: A little bit about Ankura – we are a professional consulting firm with 1400+ people. We have offices throughout the world – primarily United States, but we also have offices in Hong Kong and we’re building one up in Australia, and a couple of other places. I’m part of the cybersecurity division and we have about a hundred professionals in that division, which encompass digital forensics, incident response, eDiscovery, data analytics, and our proactive services where they do instant response plans, cybersecurity assessments, and more. Now I’m going to flip it over to Brian Heun and let him introduce himself and KMRD Partners.
Download our Cyber Security Assessment PDF to learn more about the assessment and benefits.
Brian: Thanks Clay. I’m Brian Heun and I’m one of the partners here at KMRD Partners. I’ve spent 14 years in the property and casualty insurance and brokerage business and I have a CIC designation. We like to hold ourselves out as an extension of our clients’ management team by providing outsource risk management to our customers. KMRD Partners is a regional boutique firm out of Warrington, Pennsylvania. We have three offices in Pennsylvania and we frequently act as not only support but as a risk management department for our clients – not only in insurance placement, but contractual risk transfer, and claims management. Insurance is the most expensive way to transfer risk and we spend a lot of our time helping our customers transfer or deflect risk from their business.
Clay: Thanks Brian. Today, we’re going to talk to you about social engineering. We’ll discuss the different types of social engineering attacks that can occur and a little bit about how to protect yourself from attacks. And then we’ll flip it over to Brian where he’s going to talk about insurance and related assessments.
Clay: So what is social engineering? When we talk about social engineering we’re referring to information gathering. This can either be done by you providing it, by somebody tricking you into providing it, or you just posting it up. When I was in law enforcement, we used social engineering for a lot of things. When I worked undercover narcotics, we used social engineering to find known associates, to find out where people were hanging out, and to find family members.
Clay: If we knew somebody was wanted, we knew where to go look for them – probably at their family members’ house. When I started getting into the digital forensics world, we started using that to crack passwords and password protected files. The bad guy has his various files locked up where he thinks they’re protected. But usually people are creatures of habits. They’ll use dates of birth in their passwords or their names of their spouses, their children, or their pets. It’s usually going to be some iteration of that. Cyber criminals, just like with any other tool, they can take something that is typically used for good and turn it around and use it for bad. Criminals can use social engineering to gain access to your network.
Clay: There are a few Social Engineering initial data sources. Unwitting people can just automatically give up information or can be tricked into giving up that information. One of the easiest ways to gather information is social media. You can go look at anybody’s Facebook page that you know, and people are posting all kinds of personal information on their birthdays. How many friends do you have that show the birthday pop up? I don’t put my birthday on there because I know that people can use that information against me. Cyber criminals will browse dating sites, and even LinkedIn, to gather information for their phishing attacks. Or, they can actually use previously compromised business contacts or other entities. We see this a lot with email compromised cases.
Clay: The different types of social engineering that we’re going to talk about today are Baiting, Phishing and Spear Phishing, Vishing, Tailgating, Pretexting, and Quid Pro Quo.
Baiting
Clay: Baiting. Imagine you are going on a fishing trip and you have this brand new shiny lure – that lure is the bait – and you throw it out and expect the fish to grab at it. People are like fish – and you can do this as an experiment. Take a flashy gold or silver drive and just throw it at the front door of your office and see who picks it up. I can guarantee you that somebody – eventually – is going to stick it into a computer. Why? Because people are curious. Criminals do this. They will take a USB flash drive and put some malware on it – usually an auto start malware. They’ll expect somebody to pick it up and walk into their business and drop it onto their system. Or they may put some malicious documents on it with an enticing name – maybe something like “Pay Raise PDF”. Eventually, inevitably, somebody is going to click on it. Why? Because people are creatures of habits. They’re curious and they want to see it.
Call the Incident Response Hotline 1-800-496-0089 or email Incident@ankura.com
Clay: There are a number of ways to reduce the risk and impact of a cyber attack. End user education, and up-to-date antivirus protection, are the most effective ways to prevent a lot of these attacks. Antivirus is a great tool and is something you should have in your tech environment. But keep in mind, it’s only good for what came out yesterday, or what it can see heuristically, and there’s a lot of new malware out there that just doesn’t get detected. Another way to protect yourself is to limit user privileges. We don’t want to give somebody administrative rights to a computer if they don’t need it – because if their account is compromised then the bad guy has access to it. Disabled block macros is another way to protect yourself. You’ll see this a lot – malware is built into a word document and it needs those macros in order to execute. Blocking macros adds a level of protection. Additional ways to protect yourself are to disable auto runs and don’t allow external USB devices. You can set it as a security policy to not allow external devices. That might be extreme – but if this scares you, then it may be the way to do it.
Phishing and Spear Phishing
Clay: This is probably one of the most common tactics used by cyber criminals. I don’t know how many times I’ve been through the mandatory security training that our company provides – but the human factor is just something you can’t always fix. People are curious. The threat actor will create the email, and it’s going to look legitimate – like it came from a trusted source. The goal is to get you to click on the link or open something so that malware gets dropped onto your system.
Clay: Here’s an example of a fake Office 365 email. This was actually a real email. I’ve changed the names to protect the innocent of course. I’ve boxed out a few things you could easily look for to identify this is a fake. This email did not come from Outlook – as you see from the return address. Notice the common misspellings and see how it says “validate your email”. Companies really won’t ever ask you to do that. And the other thing is you can right click and hover to look at the hyperlink and see what it says.
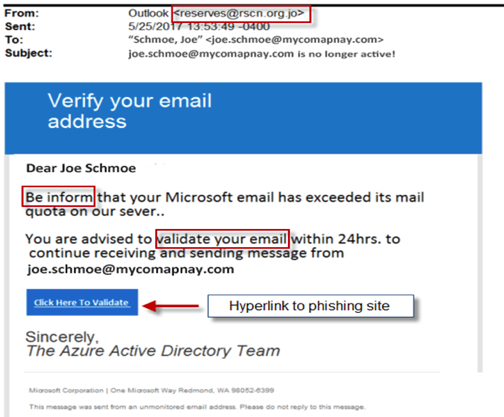
Clay: Notice this next one is not coming from Microsoft – it’s not even an actual address – so it’s probably not legitimate.
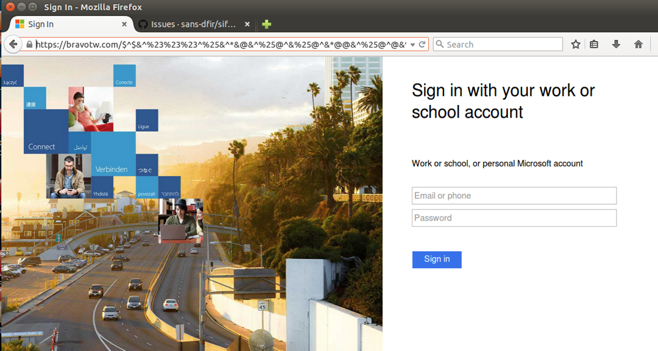
Clay: And here’s an example of a fake Docusign link. Notice the address bar. That is a red flag right there, but at least this attacker was nice enough to give you an option of what email platform to use.

Clay: In this particular instance, I selected Office 365. When I clicked on that option I was presented with a login page that looks just like an Office 365 login page. But then look at the address bar. They want you to enter your email address, and your passport, and then click “Sign In”. Doing so would send those credentials to the attacker and they would now have access to the email account. How do we reduce the risks of Phishing and Spear Phishing? End user education is the best way followed by using a strong email filter, making sure your antivirus is up to date, and also limit your user privileges and disable and block macros.
Vishing
Clay: Vishing is the voice version of Phishing. Everybody gets those calls – those fake Microsoft support calls. I get them all the time. I have a virtual machine with an FBI logo on the back. So I”ll boot up the VM and give them access and then yell at them “I got you now” and then they hang up. So just a little fun that I have. To reduce the risk of Vishing get end user education. Microsoft’s not going to call you. The IRS is not going to call you. Teach your people this. And fake tech support – we see that all the time – so train your people who your real tech support is and also limit your user privileges as well.
Pretexting
Clay: Pretexting is actually a subcategory of Vishing or Phishing. A real world example of this – when I worked for IBM, we had a client who had a large bank transaction go through. They just didn’t know how it happened. So we started looking at the user’s computer and we found that they were infected with Dridex. Dridex injected code into the web browser so when you went to a banking website – and it was one of the banks that this malware knew about – it would inject a little pop up window that said, “call this number to validate your account”. When a person calls that number someone answers, posing as a bank employee, and they trick you into giving up your log in credentials. Now, the criminal can go in and do the large transfer. Again,…to reduce the risk, employee education and limit user privileges.
Tailgating
Clay: Tailgating – I don’t know how many times I’ve seen this. , I’ve been on client sites on many occasions and just been able to follow people in. Especially if we’re there for an assessment or something, we can just walk right in. You can pose as a FedEx delivery or a food delivery and just walk right on in. People leave their computers open and passwords written down on the desk. These bad guys can just get it.
Clay: Employee education helps to reduce risks associated with tailgating. Also, keep the unattended systems locked, limit your user privileges, keep your antivirus updated, and disable your auto runs. And of course don’t allow USB drives because we don’t want the bad guy walking into the building and sticking in his own USB drive.
Quid Pro Quo
Clay: Quid Pro Quo occurs when the threat actor requests confidential information in exchange for something else. An example would be – someone’s going to give you a cruise in exchange for a password. If it’s too good to be true, remember it probably is. So again, employee education and limit user privileges, that’s the best way you can prevent most of this. Now let’s flip it over to Brian at KMRD Partners to discuss insurance coverage.
Brian: Thanks Clay. As Clay discussed, there are many different types of social engineering schemes. However, today’s most prevalent reason to attack is to gain funds or money. And so, we’ll talk about where the coverage is in your policies.
Brian: If you are like a lot of our clients, they might say “don’t I buy a property policy for damage to our network or access to funds? If you buy, a lot of our clients say, well, don’t I buy a property policy for damage to our network or, or theft of funds? And, that’s not typically the case.
Brian: From a coverage perspective, you can buy for social engineering in several different ways. One way is kidnap and ransom. On really large global properties, you might see some cyber coverage or privacy coverage – which also will include social engineering. However, most likely you’re going to see it on crime and cyber policies. And the coverage for both of these policies is changing drastically and very quickly.
Brian: Coverage looks a lot different than it did even 12 months ago. That’s how quickly it’s moving. I’ll give you an example of the growth in funds transfer fraud. A Micro Trend report suggested $9 billion of estimated reported losses in 2018. In 2013 it was $3 billion. The legal landscape is also changing for this type of coverage. And Michigan and New York are both leading the way in defining direct loss – whether the computer fraud crime triggered, or happened, and the proximate cause of the fraud to a computer system.
Pros/Cons of Coverage
Brian: See the chart below for some of the reasons that you want to make sure that you’re identifying the proper coverage, whether it’s crime or your social engineering coverage. This chart shows you some of the pros of putting social engineering insurance coverage – and paying for funds transfer type fraud – on a cyber policy.

Brian: The cyber policies claim trigger is a fraudulent instruction – as opposed to a direct proximate cause of loss for a computer fraud in a crime policy. The cyber policies typically have a demand for cryptocurrency, which is important. A crime policy trigger may require demand of monies or securities. That’s an important distinction. Typically you’re not going to find any voluntary parting, which means you voluntarily gave someone funds because they either asked for it or tricked you into giving it up.
Brian: Where a crime policy may include that type of exclusion, cyber policies – social engineering events – can include loss of data, not just loss of money and securities. That’s a good reason to have this type of coverage – where somebody might try to steal data rather than funds.
See also: KMRD Cyber Risk Management and Insurance
Brian: From a cons perspective, notice crime policies, include erroneous transfer. This is where employees actually make a mistake. Maybe they put in the wrong routing number and that triggers the loss. This would be something that would be found on a crime policy, but perhaps not a cyber policy. Third party coverage – cyber policy is only going to cover loss of money if it’s the insured (the person on the policy or who bought the policy). For crime policies, there are options to add agents coverage for third parties holding money.
Brian: Consider a payroll company – they might be withholding tax dollars on your behalf and they may withhold it for a month and then make those payments on your behalf. Anybody who is prepaid freight, or anyone who is holding your money in advance, that’s an example of where you can get some underwriting on a crime policy but not on a cyber policy. Some policies require authentications of funds. I recently read about a program in a fairly large organization that is required to authenticate the request. Well, in my opinion, that eliminates the reason why you should buy a cyber policy for computer fraud coverage. The advent of more regulation – we’ve got the Nevada/California version of GDPR. It certainly could dilute cyber limits as coverage and claims continue to evolve.
Brian: And then, finally, you might not be able to buy high enough limits for fraud coverage on a cyber policy – whereas you typically can with a crime policy (if you spend enough money). When looking to your broker to provide you with both of these coverages (cyber and crime), you need to coordinate the other insurance clause. A few weeks ago, I read a potential clients’ policy – both policies were listed as “in the event of other insurance in a claim we are excess”. Well, that’s a problem because, in event of a claim, Carrier A is going to point to Carrier B, and vice versa. And you don’t want that.
Brian: If you don’t buy coverage now, I recommend at the very least, that you fill out an application for coverage. Typically there’s a three page application that you need to go through and they ask a series of questions about your infrastructure.
Brian: And just filling out the application and learning a little bit about your infrastructure and your network will show you just how protected you think you are versus what the norms are. Keep in mind, just because you might not be doing every single best practice – or answer a “no” on that application – doesn’t mean that you will be turned down automatically for insurance coverage. It’s just a means to underwrite the program.
Fill out our Cyber Risk Insurance Application for coverage.
Brian: I suspect costs are going to double in the next five years because of the claim activity. Chubb, one of the leading providers, has a loss ratio of approximately 50%. They’re still making money today but I have a feeling that things are going to change.
Brian: KMRD partnered with Ankura and an “A” rated player in the insurance space for cyber to offer our clients up to a 20% discount on cyber insurance. Here’s how it works. Ankura does an assessment to identify critical vulnerabilities within your network, policies, and procedures. The insurance company will give you a 5% discount on your policy for just going through the assessment process. If you are able to remediate or fix the critical vulnerabilities (only the critical because there might be many others listed) the carrier is willing to extend an additional 15% (making it a total of 20%). There is no other program like this in the marketplace today. On top of that, you get a pre-negotiated policy coverage form with enhancements (that normally would take approximately nine months to get).
Brian: Once again, full coverage is evolving, but this is a real benefit to address your potential vulnerabilities. And you get pre-negotiated coverage at a discounted rate.
Contact Brian Heun at 267-482-8309 or email bheun@kmrdpartners.com to have an expert review of your cyber and crime coverage or to find out more about cyber insurance discounts for your business.
Social Engineering Webinar Q&A
The questions and answers below have been lightly edited for context and brevity.
Question: What do you believe employee training should include? How often should training be conducted?
Answer: Employee training should include some ways to recognize how these attacks occur. Put these concepts in front of your people. There are many free training sites out there that can walk you through a lot of this. Just Google “free employee cybersecurity training for employees” and these sites will pop up. Make sure to do the training once per year – so it stays fresh.
Question: Are the terms and conditions of a cyber or crime policy drastically different? Why does one cost 20% more?
Answer: Each policy is customizable and each carrier’s policy form is different as well as their offering. There is no standard policy. Costs typically vary by carrier due to the terms and conditions as well as the support team they deploy in the event of a claim. As an example, some cyber insurers use in house response experts and some outsource to organizations such as Ankura.
Question: Why would I buy social engineering coverage in both a cyber and crime policy?
Answer: While there may be overlap or excess coverage, the terms and conditions can be different. As an example – no 3rd party coverage in a cyber policy, only loss of money if it’s the insureds. Crime policy can add agents coverage for 3rd parties holding insureds money.
Question: Why can’t I transfer my risk contractually to my clients, vendors, and others?
Answer: It is very difficult, if not unfeasible to transfer the negligence of your own employee in a voluntary parting of funds. Training and insurance is the best route. For more info on this topic please visit https://www.linkedin.com/pulse/can-you-transfer-your-cyber-privacy-risk-brian-heun-cic/





