Social Engineering and How To Protect Your Computer From Hackers, Viruses, and Spies
While Social Engineering may sound like a way to encourage people to mingle at a dinner party, it is actually a devious plot created by hackers and spies to infiltrate your computer and business networks through a number of nefarious tactics, including the following:
Phishing
Chances are you’ve been the target of a phishing attack on numerous occasions, as this is the most common type of attack employing social engineering techniques. Attackers have at their disposal a grab bag of vehicles including e-mail, social media and instant messaging; using them to trick you into providing sensitive information or even inviting you to visit malicious web destinations to compromise your companies’ information systems.

Phishing attacks typically share a few characteristics:
- Messages are designed to attract your attention by stimulating curiosity regarding a topic and directing you to visit a website to gain additional information.
- Messages attempt to gather your user information by presenting a sense of urgency. These messages attempt to trick you into disclosing sensitive data to resolve a situation that could only get worse absent a timely response. For example, messages can claim knowledge of visits to pornographic websites. The perpetrator then threatens to share this evidence with your entire address book unless a bitcoin ransom is received.
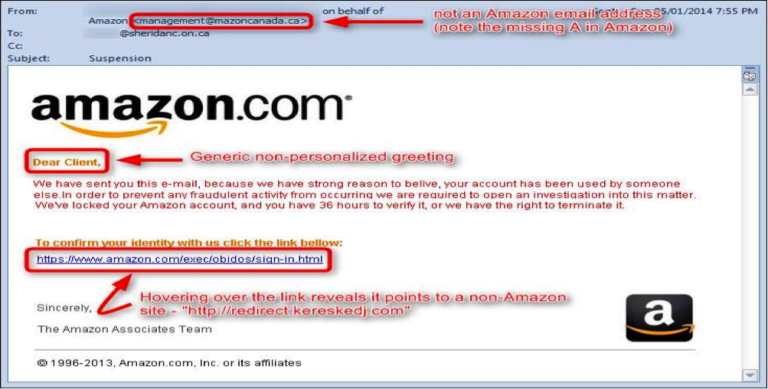
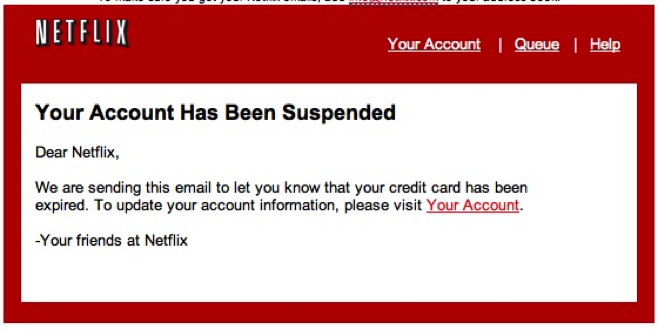
- Phishing e-mail messages typically include a deceptive subject line to trick the recipient into believing the e-mail has been sent from a trusted source.
For example, the subject line could say, “This is interesting.” To achieve the desired deception, attackers will often use a forged sender’s address or the spoofed identity of an organization. Perpetrators will typically reproduce contents such as texts, logos, images and graphic styles included on a firm’s legitimate website as they seek to achieve authenticity. However, also typically, spelling mistakes will often expose the fraud.
Below are two examples of phishing emails.
Watering hole
In a watering hole attack, the perpetrator targets an entire group of users bound by a shared interest by injecting malicious code into a web page typically visited by many members of this group. When you visit the page on the compromised website, a backdoor Trojan is installed on your computer. As the name suggests, the predator lurks nearby as you approach and eventually enter the web page – and then “wham!”. Much like what happens to the zebra while drinking near a real-life watering hole.

Pretexting
Pretexting names the practice of assuming a fake identity to obtain information from an unsuspecting target. To be successful, the perpetrator must first build trust with you. For example, the perpetrator can pose as a representative of your trusted bank or brokerage firm. The perpetrator can claim to have discovered irregularities in your account and request your login credentials in order to correct the situation. Pretexting attacks often target victims whose mental acuity has been diminished by age.
Baiting and Quid Pro Quo
Baiting attempts to trick you with the promise of a good. A common instance is a scenario in which the perpetrator offers a malicious file disguised as a software update. Flash updates are commonly promised.
While a Quid Pro Quo attack is a type of baiting, instead of baiting you with the promise of a good such as a Flash upgrade; quid pro quo offers a service or benefit in exchange for your information or access.
A perpetrator who impersonates an IT staffer is the most common quid pro quo attack. The perpetrator contacts you by phone to deliver an upgrade or software installation. The perpetrator even ask you to facilitate the operation by temporarily disabling AV software to install the malicious application.
Join our FREE Webinar on January 29 at 12pm (ET)
As the scale and complexity of cyber intrusions and attacks increase, we believe it’s important to transfer risk to insurance coverage and also develop a comprehensive protocol to address IT gaps before cyber intruders infiltrate your systems. This is why KMRD Partners and Ankura Consulting have teamed up to offer a FREE webinar on social engineering.
During this webinar, our experts will:
- Explain social engineering and top threats in 2020.
- Discuss the various types of cyber attacks.
- Review the methods used by social engineers.
- Reveal strategies for avoiding psychological manipulation.
- Learn where to find social engineering computer fraud coverage – the most common type of loss associated with social engineering.
- Discuss the benefits of a network assessment, including cyber policy discounts by an insurance company.

Capacity is limited so join early. Our virtual doors will open 15 minutes before the scheduled start time. Feel free to invite your friends and colleagues that might be interested in Social Engineering, too.

Social Engineering Webinar
When: January 29, 2020 12:00 PM Eastern Time (US and Canada)
Topic: Social Engineering Webinar: How Criminals Exploit Human Behavior and How to Protect Your Enterprise
Register in advance for this webinar:
https://zoom.us/webinar/register/WN_9j7-uvrbT_eWueMfj2rNyQ
After registering, you will receive a confirmation email containing information about joining the webinar.
What is Social Engineering?
Social Engineering is the art or act of information gathering either by tricking someone to provide information or by using available information to achieve a task.
The term covers a broad range of malicious activities to trick users into obtaining personal and sensitive information or gaining access into systems to exploit the network, company, and its people.
In our webinar, we’ll discuss the most common types of social engineering attacks, including: Baiting, Phishing (and Spear Phishing), Vishing, Tailgaiting, Pretexting, Quid pro quo. We’ll show you how hackers pose as others or manipulate employees to gain access into your networks and then create backdoors to launch Denial of Service attacks on your business.
In addition, we’ll share tips on how to improve your defenses against social engineering. We’ll also provide you with a premium policy discount when you have Ankura assess your network, organization, procedures, and policies.
Download our Cyber Security Assessment PDF to learn more about the assessment and benefits.
Here are the event details again.
Clay and Brian are going live with this special webinar on Wednesday, January 29 at 12pm. The event will start promptly at 12 p.m. ET.

We hope to see you there. In the meantime – take a minute to drop any questions about this webinar to us at bheun@kmrdpartner.com. We’ll be taking a look over them in the next few days, and one of your questions could be covered at the event!




